
Scalpers have stolen tickets to museums and concerts this summer. Organizers, museums with decisioning engines, can develop a set of rules to identify and intercept potential scalpers.
When making the rules, the comprehensive analysis of multiple factors, such as IP address, Device Fingerprinting, account association, and behavior pattern, should be considered to improve the accuracy and reliability. At the same time, we should effectively intercept the scalpers, and try to avoid causing inconvenience to normal users. It is necessary to analyze according to the actual business situation and user behavior, so it is necessary to set the threshold value and restriction conditions of the rules reasonably.
Activity period rules: Set the activity period to limit the ticket purchase time window, to ensure that scalpers cannot obtain and hoard a large number of tickets in advance.
Real-name authentication rules: Users are required to conduct real-name authentication to reduce the existence of anonymous accounts and improve the traceability and authenticity of the ticket purchase process.
Geographic location rules: According to the user's geographical location information, set the ticket purchase restriction rules for specific areas to limit the ticket purchase behavior in unauthorized areas.
IP address restriction rule: set each IP address can only submit one order within a certain period of time, to prevent scalpers from using multiple IP addresses for batch tickets.
Device identification rules: monitor device fingerprint information, intercept abnormal device fingerprints (such as simulator, Root device, etc.), and restrict their access to and submit orders.
** Frequency limit rule:** set the frequency of users to submit orders, for example, limit the same user can only submit a certain number of orders in a short period of time, to avoid malicious ticket brushing or bulk orders.
** Account association rules**: detect the correlation between accounts, identify the accounts that may be operated by the same equipment, the same contact information and the same payment method, and restrict them.
Account historical behavior rules: analyze the historical behavior patterns of users, such as abnormal ticket purchase behavior, frequent refunds, etc., identify potential scalpers' accounts, and strengthen the review and restriction of their orders.
Rule makers should make comprehensive analysis and decisions based on specific business scenarios and risk characteristics to ensure that the implementation of rules can be effective. Strategies and means for scalpers also need to evolve, and rules also need to be optimized and updated at any time. Based on real-time risk data and feedback information, the rules should be adjusted in time to maintain effective prevention of scalpers.
What is a risk rule?
The so-called risk control rules are a set of pre-defined logical rules used to analyze and judge the operator's behavior and identify potential risks or abnormal situations. These rules are designed according to specific business requirements and risk models, and can be defined and implemented through programming language or configuration files, and can be written using predefined semantic modules.
The rules in the risk control engine usually consof the following:
Basic rules: Basic rules refer to the most basic and commonly used rules in the risk control engine that are used to identify common risk behaviors. These rules can include abnormal access to IP addresses, abnormal changes in the device fingerprint, abnormal login of the account, etc. The underlying rules are often defined based on industry experience and common risk patterns.
Customization rules: Custom rules are customized according to specific business needs and risk characteristics. These rules can be designed for specific industries, specific business scenarios, or specific user groups to meet personalized risk identification needs. Custom rules often need to be continuously optimized and adjusted based on actual data and business knowledge to improve accuracy and adaptability.
Machine learning model: Machine learning technology can also be used in risk control engines to build models for risk judgment and prediction. These models can learn risk patterns and patterns from a large amount of historical data, and make predictions and decisions based on real-time data. Machine learning models can be flexibly trained and updated according to the changes in the data and new risk patterns, with high accuracy and adaptive ability.
How to create a risk rule?
The source of risk control rules business practice, data mining and model, enterprises can more flexibly manage and modify business rules.
Industry experience and best practice: relatively common risk behavior, build rules using industry experience and best practices. These experiences and practices are usually accumulated by professional risk control teams or practitioners, and can provide a more comprehensive and reliable risk judgment basis.
Data analysis and mining: Through the analysis and mining of historical data, the hidden risk patterns and association rules can be found. These data models can be constructed through data science and technology, and they can generate rules through statistical analysis, association rule mining, and anomaly detection, etc.
Business requirements and expert knowledge: Some specific rules can be formulated according to the specific business scenarios and requirements, combined with the experience and domain knowledge of the risk management experts. These rules can be customized according to the business characteristics and risk factors, more in line with the actual business needs.
In short, the rules in the risk control engine come from various sources, including industry experience, data analysis and mining, as well as business requirements and expert knowledge. The design and application of these rules requires a comprehensive consideration of business characteristics, risk patterns and data situations, and is constantly optimized and updated to maintain accuracy and adaptability.
Dinsight: Step-by-Step Configuration of Risk Rules
Rules ultimately need to be delivered to the operation personnel to configure and use, so it must be able to meet the flexible configuration and arrangement, and easy to understand, in order to maximize its power. The Dinsight real-time risk control engine provides a visual interface for business people to quickly get started and configure new, add, and test rules. After entering the user name and password, log on to the risk control decision engine, enter the "Policy Center-Component Management-Component Mode", and select "Rules" in the drop-down box.
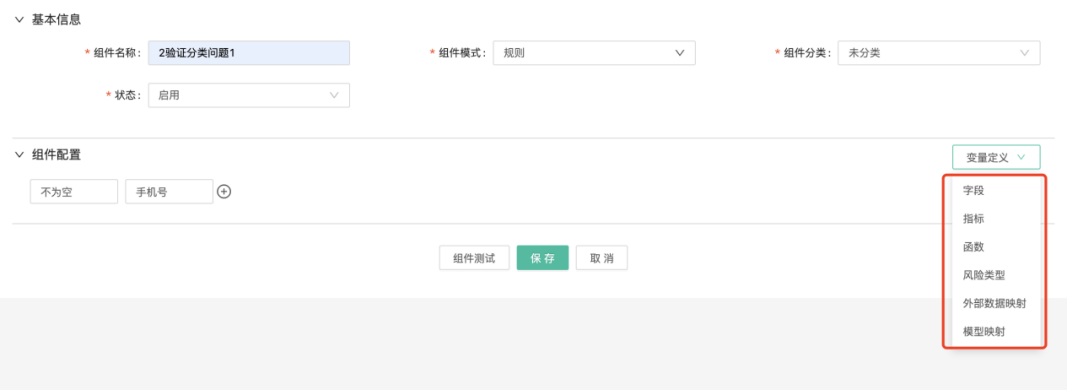
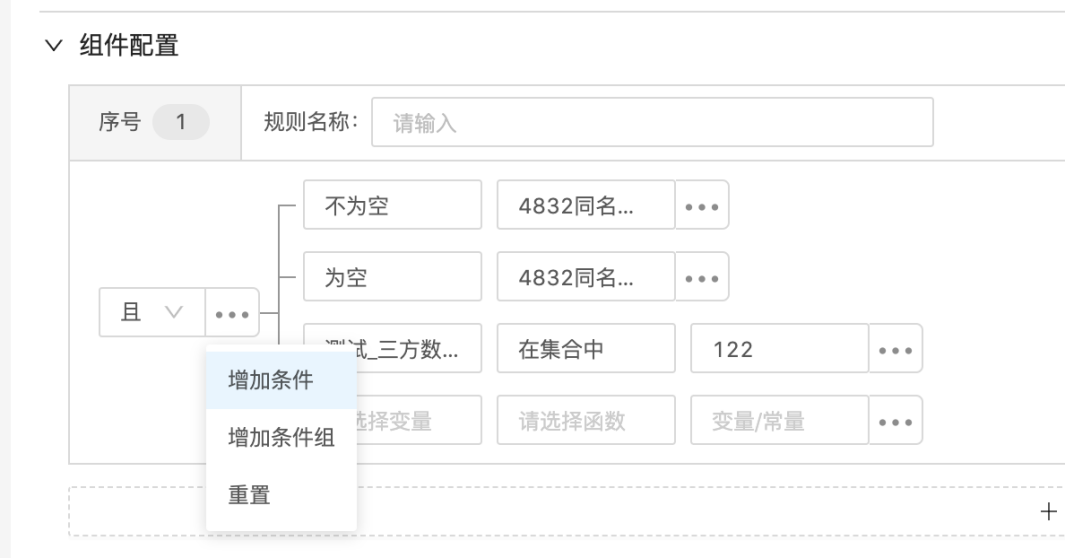
Make rule configuration in Component Configuration. The logical relationship in the configuration condition can be changed according to the actual business needs, with "and" and "or" currently available; a condition setting can be configured by default. If click "Add conditions", in "..."Add a condition setting after the button.
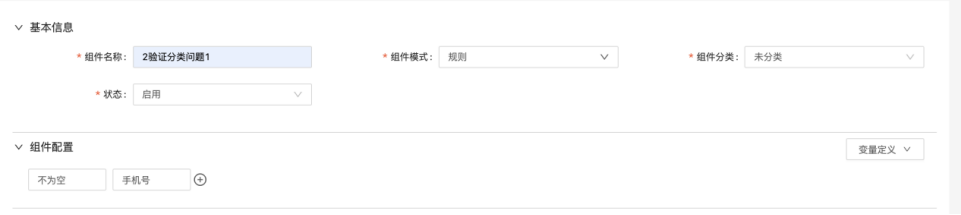
After the rule configuration is complete, it can be tested. In the "Component Configuration" interface, click the "Component Test" button to display the "Component Test" page; display the test data to be assigned in the component;
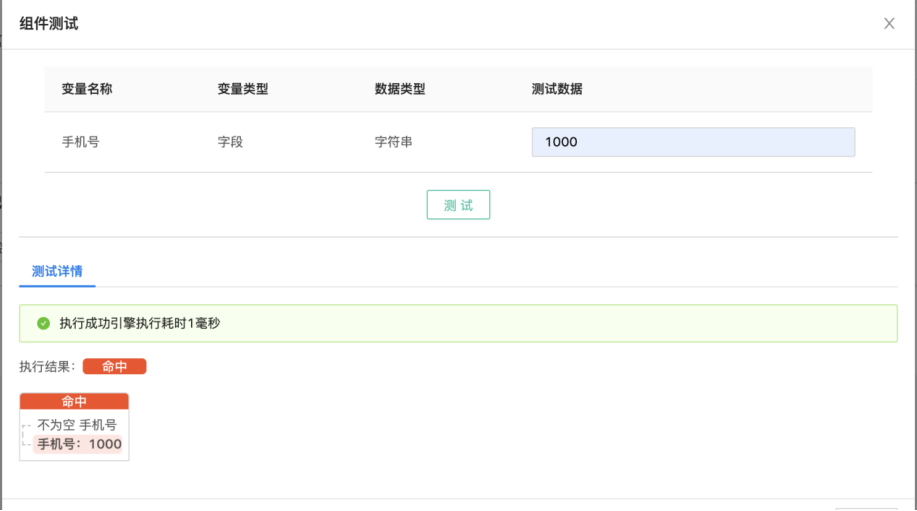
After manually assigning the variable, click the "Test" button and the component enters the test. After the test, you can view the details of the components. You can also continue to adjust the data, and test the component multiple times to verify the availability of the component.
 Dinsight The real-time risk control engine supports the rule-set configuration. In this mode, multiple rules can be set up, and each rule has a set of actions, and the rules are executed in order. Each rule hit will return according to the corresponding action.
Dinsight The real-time risk control engine supports the rule-set configuration. In this mode, multiple rules can be set up, and each rule has a set of actions, and the rules are executed in order. Each rule hit will return according to the corresponding action.
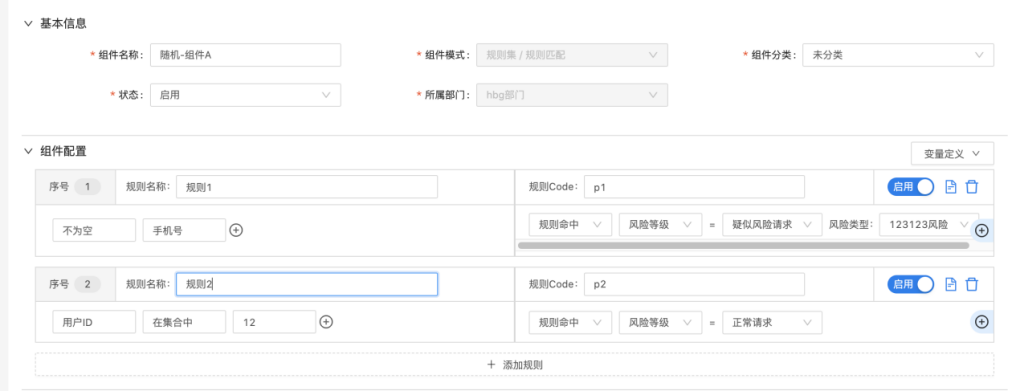
Enter "Policy Center-Component Management", click "New Component" button, select "Rule Set / Rule Match" in the drop-down box to display the configuration box of "Rule Match"; multiple rules can be added; multiple conditions and actions can be set separately in each rule.
 Dinsight can perform risk judgment on the requests sent by the business front end in marketing activities, payment orders, credit applications and other scenarios, and return the decision result within milliseconds to improve the risk prevention and control ability of the business system. The average processing speed of daily risk control strategies is less than 100 milliseconds, the aggregate data engine, the integration of expert strategies, the parallel monitoring, replacement and upgrading of existing risk control processes, and the construction of a dedicated risk control platform for new businesses; Aggregate anti-fraud and risk control data, support multi-party data configuration access and precipitation, can be configured graphically, and quickly applied to complex strategies and models; Based on the experience reserve of mature indicators, strategies and models, as well as deep learning technology, self-performance monitoring and self-iteration mechanism of risk control can be realized; Integrated expert strategy, based on system + data access + index library + strategy system + expert implementation of actual combat; It supports parallel monitoring, replacement and upgrading of existing risk control processes, and can also build a dedicated risk control platform for new businesses.
Dinsight can perform risk judgment on the requests sent by the business front end in marketing activities, payment orders, credit applications and other scenarios, and return the decision result within milliseconds to improve the risk prevention and control ability of the business system. The average processing speed of daily risk control strategies is less than 100 milliseconds, the aggregate data engine, the integration of expert strategies, the parallel monitoring, replacement and upgrading of existing risk control processes, and the construction of a dedicated risk control platform for new businesses; Aggregate anti-fraud and risk control data, support multi-party data configuration access and precipitation, can be configured graphically, and quickly applied to complex strategies and models; Based on the experience reserve of mature indicators, strategies and models, as well as deep learning technology, self-performance monitoring and self-iteration mechanism of risk control can be realized; Integrated expert strategy, based on system + data access + index library + strategy system + expert implementation of actual combat; It supports parallel monitoring, replacement and upgrading of existing risk control processes, and can also build a dedicated risk control platform for new businesses.