iOS App Defender
1. Product Introduction
AISecuriusiOS defense is a next-generation defense product based on the virtual machine source code protection technology for iOS. The executable files in iOS APP are obfuscated, along with AISecurius' original virtual machine technology to guard against decryption. Protect the integrity of App and prevent the code and resource files in the application from being tampered with.
2. Product features
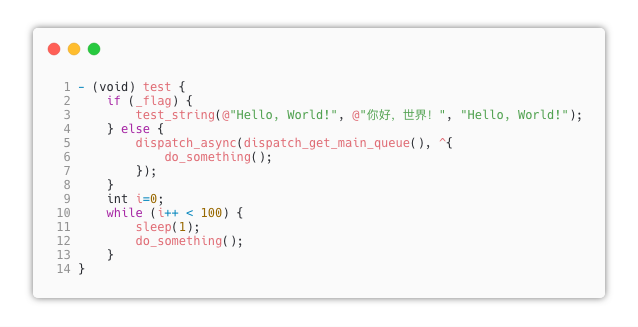
iOS defense mainly includes logic obfuscation, string encryption, and code virtualization protection. The features are demonstrated by protecting the following code snippet:
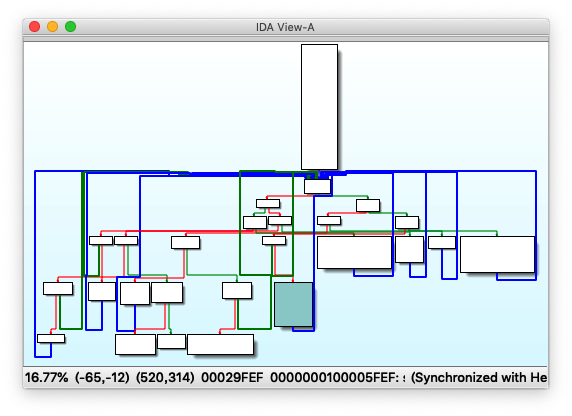
Drag the compiled code into IDA Pro for analysis to get the control flow graph. There are only 6 code blocks with simple jump logic. It's easy to judge the characteristics of if-else and while:

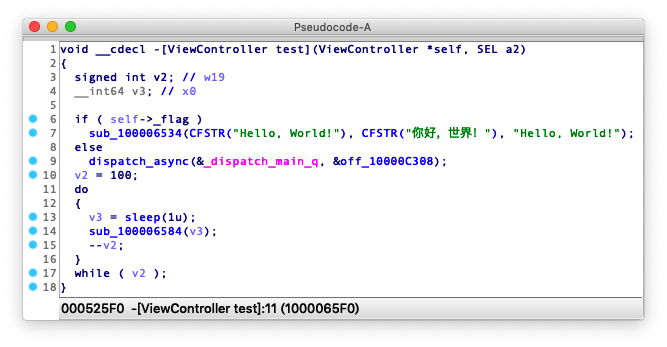
Decompiled to pseudo code, the code logic and the strings in the source code are clearly showed, which is basically the same as the source code, as shown below:
2.1 Code logic obfuscation
Make the code difficult to understand by dividing, disrupting, hiding, and inserting redundant instructions in functions without affecting the original logic.
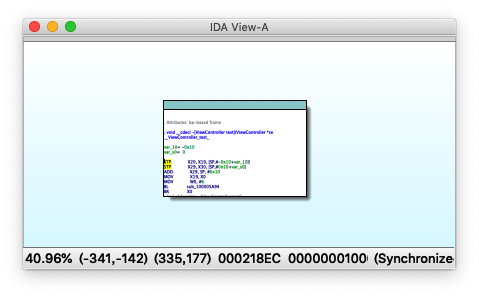
After logic obfuscation, the control flow graph of the function will become very complicated, and a large number of useless code blocks and logical jumps are interspersed in the function, which greatly increases the difficulty of reverse analysis:
If the anti-decompilation function is enabled, the control flow graph will be hidden, showing only one code block, and no valid code can be decompiled (as shown below), which is very effective against reverse analysis tools, including but not limited to (IDA Pro, Hopper Disassembler, Binary Ninja, GHIDRA, etc.)

2.2 String encryption
Encrypt all static constant strings (C/C++/OC/Swift), which is decrypted at runtime to prevent static analysis through the string and code logic guessed by attacker.
After the strings in the code are encrypted, all strings are replaced with encrypted references, and cannot be converted into plaintext strings. Strings such as Hello, World! could have been easily decompiled, but it is no longer readable after encrypted:
2.3 Code virtualization
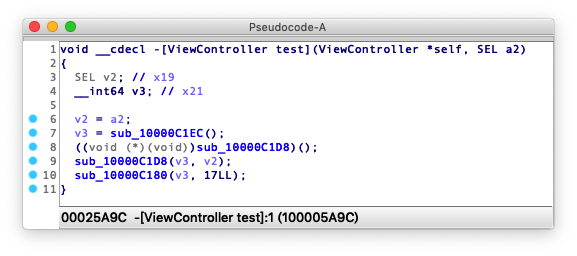
Compile the original code into dynamic DX-VM virtual machine instructions, and run on the DX virtual machine, which cannot be decompiled back to readable source code. No tool is able to decompile virtual machine instructions.
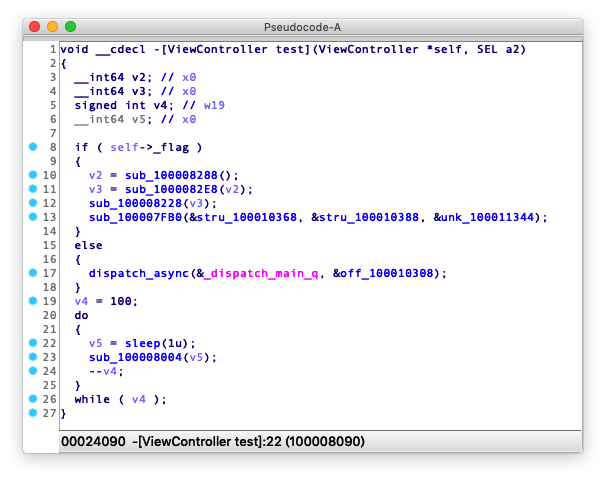
After code virtualization, the decompiled the function will not show anything that may give away original code, and the function body only contains calls to the virtual machine subsystem
2.4 Anti debugging
Prevent the analysis of application logic through debugging. The function is effective in preventing the App process from being debugged.

3. Scope of application
- Xcode: 9.0+
- iOS: Unlimited
- Languages: Objective-C(C/C++), Swift
- Official version supports:
- Apps,
.xcarchiveformat only, does not support.ipaformat
- Apps,
- Other formats supported by the privatized version (contact customer service for details):
- Dynamic library types,
.frameworkformat only, does not support.dylibformat - Static library types, support
.frameworkformat and.aformat
- Dynamic library types,
- Other requirements:
- Set
Enable BitcodetoYESinBuild Setting - Compile using
Archivemode to ensure Bitcode is successfully enabled, otherwise the compiled file only containsbitcode-marker - If Bitcode cannot be enabled, use auxiliary tools. For details, see
5. iOS Defense Auxiliary Tools -> 5.2 Enable Bitcode - The size after compression is under
2048M
- Set
4. Operating guide
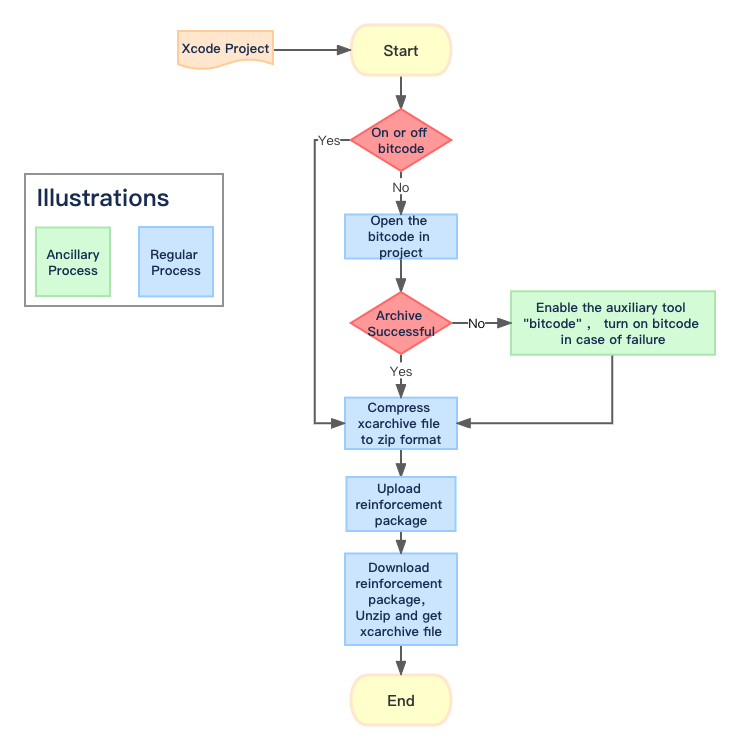
4.1 Preparation of document to be defensed
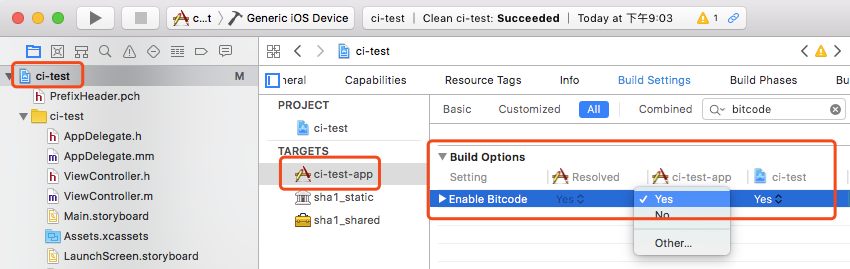
- Select the project to be protected in the Xcode project list, and select the Target to be protected in the Targets list.
- Click
Build Settingstab, search for bitcode and make sure theEnable Bitcodeoption is set toYes(for Xcode 7.0 or later, Bitcode is enabled by default)
Note: Make sure Enable Bitcode (optional) is enabled for the Target to be compiled, and all the Targets and sub-projects it relies on, add custom configuration HIDE_BITCODE_SYMBOLS = NO in Build Settings
- Set the compilation target (Active Scheme) to the Target to be protected, Device to
Any iOS Device, and click on the menuProduct->Archiveand wait for the Archive to complete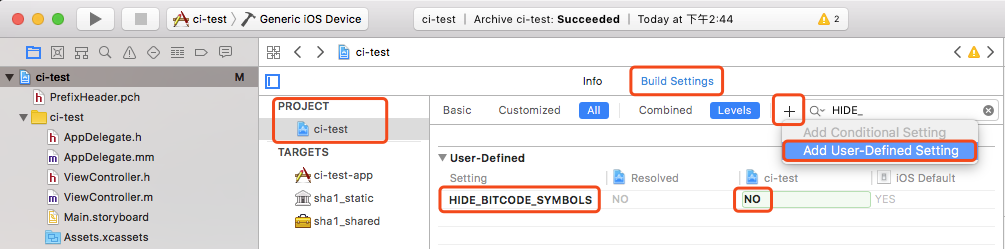
If dynamic and static libraries provided by third parties are introduced into the project, but bitcode is not enabled, the packaging will fail. In this case, use AISecuriusiOS defense tool (click to download) to forcibly enable the bitcode of third-party library. See 5.2 Enable bit code for details.
- After the Archive is completed, Xcode automatically pops up
Organizerwindow, right-click the Archive file, and selectShow in Finder. - If the file type to be protected is App, in the Organizer window that automatically pops up after Archive, right-click the Archive file and select Show in Finder.
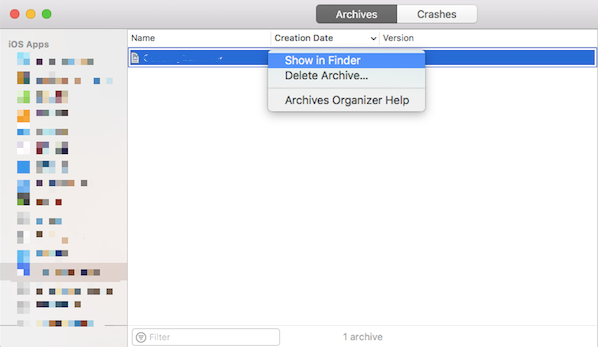
Then in Finder, right-click the xcarchive file, click "Compress..." to get compressed file in .zip
4.2 Upload defense files
- Login AISecurius control panel, and enter iOS defense page.
- Select the defense version, and click Apply, the Create window pops up
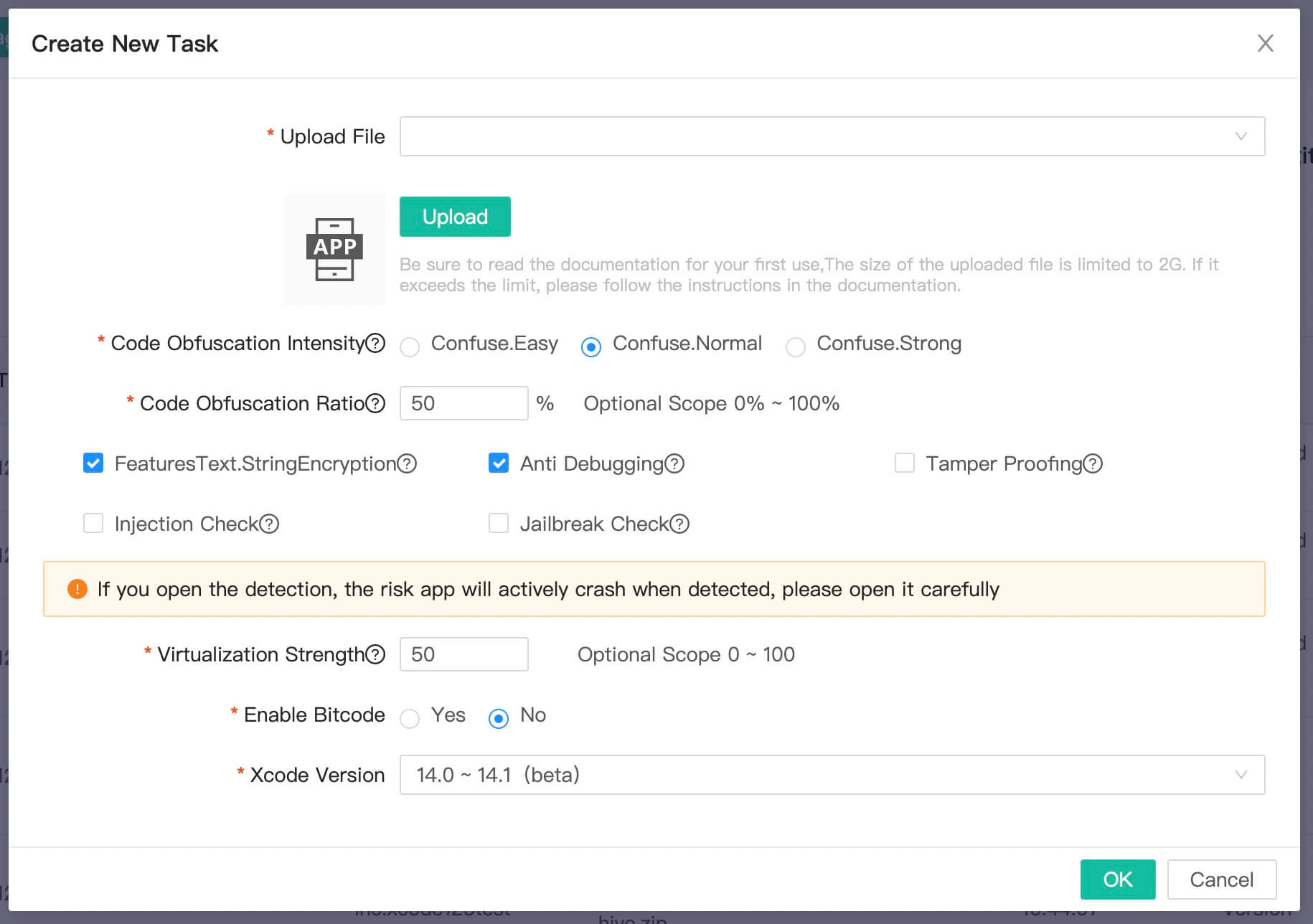
- Adjust the configuration as needed.
- Intensity of code obfuscation: For a single function, the higher the obfuscation intensity, the harder it is to decrypt, but the performance is subject to greater impact, as the code size increases, and it is not recommended to use strong obfuscation.
- Proportion of code obfuscation: Randomly select a specified proportion of functions/strings for obfuscation/encryption, and unselected functions/strings will remain the same. This option is balanced in regards of security, performance and size.
- String encryption: When enabled, all strings in the code will be encrypted, and it's impossible to export plaintext strings after decompilation.
- Anti debugging protection: Provide runtime anti-debugging for apps to prevent attacker from dynamically analyzing the logic of apps through debugging.
- Intensity of virtual machine protection: It indicates the strength of code virtualization protection. The protected code will be run in virtual machine and cannot be decompiled by any tool.
- Enable Bitcode after defense protection: It indicates whether Bitcode should be included in the xcarchive package output after defense. If so before listing on Appstore, select "Yes".
- After enabled, the package will contain both binary code and Bitcode, which will increase the size of the package, but the download size of the app is the same regardless of whether it is enabled or not.
- If Bitcode is not enabled in the original project, as Bitcode can only be enabled after defense, or it is not necessary to launch, it is recommended to select "No".
- Xcode version: please select the Xcode version used to compile the files to be defended. For earliser versions or the version is not matched, it may not be available.
- Upload files to be defended: Upload the file (.zip/.a) prepared in the first step.
- Click OK to create a task
4.3 Download the defense package
- After submitted, it will enter the waiting list. After the background processing is completed, you can download it from the task list.
- After downloaded, you will get the defense package in the same format as the source package, which is compressed package ended as .zip or static library ended as .a
- For complete xcarchive compressed package, you can decompress it directly. Double-click to import it into the Xcode Organizer, and export ipa export and submit to AppStore in Organizer.
- If the compressed package uploaded is extracted by the AISecuriusiOS auxiliary tool, you need to replace the defense package into the original xcarchive, and subsequent export or submission the AppStore is operated directly on the original xcarchive.
- If the defense fails, click "View Failure Reason" on the right side of the task list to check the reason.
5. iOS defender auxiliary tool
5.1 Features
This tool is used to assist the use of the AISecuriusiOS online defense system. Normally, this tool is not required for defense, but in some special cases, it is necessary to use this tool to perform some operations locally to assist the defnese. Click here to download.
This tool includes the following functions, and each function module is independent of each other. If one function is enabled, it does not mean that you need to enable other functions in the tool.
- Enable bitcode
- Extract xcarchive
5.2 Enable bitcode
5.2.1 Feature description
This function module is used to forcibly enable the bitcode of the third-party library. Since the AISecuriusiOS online defense tool is based on bitcode, make sure Enable Bitcode = YES when packaging. If there is a third-party library that does not have bitcode enabled in the project, the packaging will fail, and the following message will pop up:
ld: 'xxxxx' does not contain bitcode. You must rebuild it with bitcode enabled (Xcode setting ENABLE_BITCODE), obtain an updated library from the vendor, or disable bitcode for this target.
ld: bitcode bundle could not be generated because 'xxxxx' was built without full bitcode.
You can use this tool to forcibly "enable" bitcode for the third-party library as prompted in the error message.
"Enable bitcode" does not mean it embeds bitcode in the library, but deceives Xcode to make it believe that these libraries have enabled bitcode, so that it can be compiled and packaged normally. The real bitcode must be generated from the source code.
After enable bitcode using the auxiliary tool, use Xcode to open the xcarchive file and compress and upload it for defense.
5.2.2 Applicable scenario
A third-party library is introduced in the project in binary (not source code), and bitcode is not enabled for the third-party library.
If a third-party library is introduced in the project through source code, such as third-party sub-project, or the source code of the third-party library is introduced through management tools such as Pods/Carthage, set Enable Bitcode to YES in Build Settings of the Target corresponding to the library directly without using this tool.
Support third-party libraries in the following formats:
- Static Library in .framework format
- Dynamic Library in .framework format
- Relocatable Object File in .framework format
- Static Library in .a format
Support processing single library file or folder, the tool will automatically search and process all third-party libraries in the folder with bitcode disabled.
5.2.3 Operating guide
Open the AISecuriusiOS defense auxiliary tool and go to the Enable bitcode tab.
Select the file to be processed in the input box, or directly drag the file/folder to the input box, or click the input box and select in the pop-up window.
The tool will automatically determine whether the input file contains bitcode. For folder, it will automatically search all dynamic and static libraries under the file and determine whether it contains bitcode.
Click the "Execute" button, all files without bitcode will be processed, and bitcode will be "forcibly" enabled.
5.2.4 Note
The processed original file will be backed up as a .bak file in the same directory.
For dynamic libraries, after processed, it will only be used to deceive the local Xcode, so that it can successfully complete the packaging when Bitcode is enabled, however, the package cannot be directly used to submit to the AppStore. Otherwise, you will receive an Invalid Bundle prompt. It requires to be processed with AISecurius before submission. (not applicable for Static libraries and Object files)
After processed, when creating a defense task, please set Enable bitcode after process to No
5.3 Extract xcarchive
5.3.1 Feature description
This function module is used to complete the compression of xcarchive and the replacement of defense files. AISecuriusiOS online process has size limit of uploaded files. If the size exceedes the limit after xcarchive compression, use this tool to extract the necessary information to reduce the size of the compressed package. After the process is completed, replace the downloaded package with the original package.
5.3.2 Applicable scenario
The package to be processed is in xcarchive format, and the compressed size exceeds the upload limit (currently 500M). If the limit is not exceeded, you do not need to use this tool.
5.3.3 Operating guide
- Enable the AISecuriusiOS defense tool, and switch to the "Extract xcarchive" tab, and follow the insturctions:
- Select the xcarchive file to be processed in the xcarchive file input box, you can directly drag the xcarchive file to the input box, or click the input box and select in the pop-up window.
- The output path is in the same directory as the selected xcarchive by default, click the output path input box, you can select other paths in the pop-up window to modify.
- Click the Extract button, the tool will extract and compress the necessary files, and save as the files specified in the previous step.
- Access the AISecurius control panel and use the files extracted in the previous step.
- After the process is completed, download the defense package, drag it to the defense file path input box, and click the Replace button, the processed binary file will be automatically replaced in the original xcarchive.
5.3.4 Note
- When replacing the defense package, back up the original xcarchive package if needed, use the extracted zip file to restore it.
- After the extraction is completed, close the tool, and open it after the process is completed. When replacing, select the previously extracted xcarchive at the xcarchive file.
- If the skize of the extracted compressed package (containing only the binary files necessary) exceeds the maximum limit, the online defense system will be unavailable.