
During the National Day holiday, a large number of videos featuring "Lei Jun's AI voice" appeared on short video platforms. In these videos, "Lei Jun" sharply commented on popular topics such as traffic jams and holidays, and some even contained inappropriate language. Besides the complaints, the "Lei Jun" in the video also claimed to be investing in a certain university.
AI has been widely applied in many fields, from generating images and videos to answering online queries, leading to a wide array of content. When ordinary people can easily use AI to impersonate celebrities and mass-produce audio and video, it inevitably brings problems like information distortion and cognitive confusion to society.
According to The New York Times, AI-generated images of Elon Musk have appeared in thousands of fake advertisements, resulting in billions of dollars in fraud cases. An 82-year-old retiree, Tiv Beauchamp, saw a “real interview” with Musk online. In the video, Musk endorsed an aggressive investment opportunity that promised quick returns. The lip movements and voice were highly synchronized, making the video seem very real. The elderly man, believing it to be authentic, contacted the company behind the ad and followed their guidance to set up an account. Over the following weeks, the elderly man spent his entire retirement savings in a series of transactions, ultimately investing over $690,000 (around 4.95 million RMB). Unfortunately, all this money was swindled by scammers, leaving the man devastated.
These 10 Celebrities Are Frequently Impersonated by Scammers
The advent of AI has completely transformed many industries. Using AI to easily forge the likeness and voice of celebrities is not only used in phishing scams but also to promote fraudulent products, steal personal information, and trick people into downloading malware. Fans often find it difficult to tell if the content is real or fake.
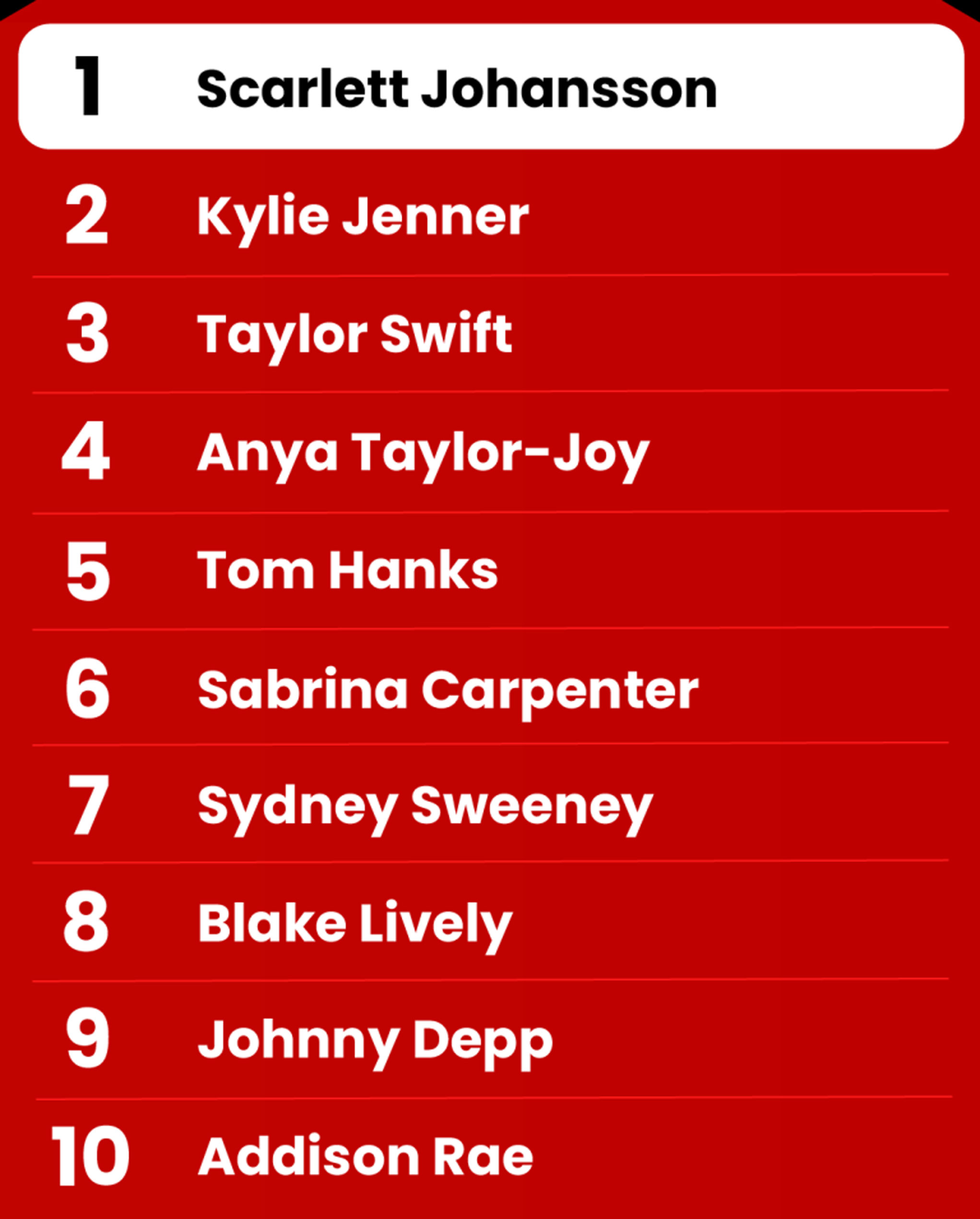
Social media is an essential platform for marketing and advertising, making it a prime channel for scams. In a report released by the security company McAfee, they listed the 10 most impersonated American celebrities. Criminals exploit their image, voice, and reputation to conduct phishing, cryptocurrency fraud, ticket resale scams, false event promotions, spread misinformation, and promote malware.
- Scarlett Johansson: Actor and singer, her name and likeness have been used by scammers for false advertising endorsements.
- Kylie Jenner: Reality TV star, her name and likeness have been used by scammers in giveaway scams, fake product promotions, and phishing websites.
- Taylor Swift: Singer, her name and likeness have been used by scammers for fake endorsements, ticket scams, giveaways, and spreading false information.
- Anya Taylor-Joy: Actor, her name, likeness, and social media accounts have been used by scammers in giveaway scams and spreading false information.
- Tom Hanks: Actor, his name and likeness have been used by scammers to promote fake “miracle cures” and fraudulent medical treatments.
- Sabrina Carpenter: Singer, her name and likeness have been used by scammers in fake ticket scams and the creation of explicit apps.
- Sydney Sweeney: Actor, her name and likeness have been used by scammers in cryptocurrency scams.
- Blake Lively: Actor, her name and likeness have been used by scammers in weight-loss gummy scams.
- Johnny Depp: Famous actor and director, his name and likeness have been used by scammers for fake endorsements, fraudulent gifts, and cryptocurrency scams.
- Addison Rae: Top social media star, her name and likeness have been used by scammers for fake endorsements, fraudulent gifts, and cryptocurrency scams.
How Ordinary People Can Identify Fake Celebrity Ads
How can ordinary people identify fake celebrity ads? There’s no simple answer, but some essential measures can help maximize the chances of detection.
- Social media platforms are hotbeds for misinformation and online scams. Be skeptical of shocking or too-good-to-be-true claims, especially when celebrities are involved. Don’t forget to use common sense and logic.
- Carefully check for unnatural features in the content – strange blinking patterns, mismatched audio, or distorted body parts could be signs of deepfakes.
- Verify the claims by cross-referencing with trustworthy news outlets and websites. Do not believe content without first performing fact checks.
- Before making decisions or purchases, consult with friends, family, or colleagues. It’s best to do some deep research and not take the promoter’s word as gospel, even if it’s Elon Musk.
- Don’t comment, share, or even click on unverified social media posts. Interacting with accounts impersonating celebrities increases your risk of being scammed.
- Never submit your personal details to unverified individuals, websites, or apps.
Social Media Platforms’ Defense Against Fake Celebrity Ads
In addressing the problem of fake celebrity ads and information on social media platforms, Dingxiang Defense Cloud Business Security Intelligence Center suggests that first, accurately identifying fake accounts is crucial to effectively preventing fraud.
-
Identify abnormal devices: Dingxiang's Device Fingerprint technology records and compares device fingerprints to distinguish between legitimate users and potential fraudsters. By uniquely identifying each device, it can detect maliciously controlled devices such as virtual machines, proxy servers, and emulators. The technology analyzes whether devices exhibit abnormal behaviors, such as multi-account logins, frequent IP address changes, or frequent modifications to device attributes, which deviate from user habits. This helps trace and identify fraudsters’ activities.
-
Identify abnormal account operations: Remote logins, device switches, phone number changes, and suddenly active dormant accounts require enhanced frequent verification. Additionally, continuous identity verification during sessions is critical. Keeping persistent checks ensures that the user's identity remains consistent throughout use. Dingxiang’s atbCAPTCHA quickly and accurately differentiates between human operators and bots, precisely identifying fraudulent activities, monitoring in real-time, and intercepting abnormal behaviors.
-
Prevent fake videos with face-swapping: Dingxiang's full-chain, panoramic facial security threat awareness solution intelligently verifies through multiple dimensions, including device environment, facial information, image forgery detection, user behavior, and interaction status. It quickly identifies more than 30 types of malicious attack behaviors, such as injection attacks, live body forgeries, image forgeries, camera hijacking, debugging risks, memory tampering, root/jailbreak, malicious ROMs, and emulators. Once fake videos, false face images, or abnormal interaction behaviors are detected, operations are automatically blocked. The video verification intensity and user-friendliness can be flexibly configured to dynamically adjust the verification for normal users while strengthening it for suspicious ones.
-
Detect potential fraud threats: Dingxiang's Dinsight helps enterprises conduct risk assessments, anti-fraud analysis, and real-time monitoring, improving the efficiency and accuracy of risk control. Dinsight’s daily risk control strategy has an average processing speed of under 100 milliseconds and supports the configurable access and accumulation of multi-source data. Based on mature indicators, strategies, and model experience reserves, as well as deep learning technology, it achieves a self-monitoring and self-iterating mechanism for risk control performance. Paired with Xintell, a smart model platform, it can automatically optimize security strategies for known risks. Using risk control logs and data to mine potential threats, Xintell allows for one-click configuration of risk control strategies across various scenarios. It standardizes the complex processes of data processing, mining, and machine learning, providing a one-stop modeling service from data processing and feature derivation to final model deployment.


