
Tracking is a key service provided by the digital platform. Whether it being PC Internet era, mobile Internet, or rapidly growing metaverse, the platform requires different technical tools to distinguish authenticity, track operations, understand users, and guarantee security. Authentification, in particular, is the premise and base of effective services, as valuable services are based on real data.
Device fingerprinting emerges with the development of digital technology
In the PC Internet era, the normal way to access websites is through browser on PC, and Internet companies use cookies and IP addresses to identify user devices. Cookie first appeared in the 1990s. The technology is used to record and track user access records, times, computer information and account information. It has become an important tool for online advertising service providers to identify users, and is widely used for the identification of devices on the Internet.
As Cookie saves user data in local storage, malicious users can easily bypass detection by clearing local data, making its application greatly limited. At the same time, due to increasing concerns about user privacy protection, mainstream browser manufacturers have gradually phased out cookie technology.
In the mobile Internet era, users have more ways to access the Internet, making it difficult to identify and track users. Also, the Internet and new technologies have made faking identity easier, which means more complicated to tackle it. Cookie technology is no longer a reliable way to identify users in the current network environment.
When it's unable to identify the user quickly, one can turn to the suspicious Internet device, and respond to high-risk devices and related operations in a timely manner, which may lead to controlled risk and reduced loss. Device fingerprinting can distinguish the authenticity of the operator, separating valuable user from malicious fraud. Device fingerprinting, which collects device, network, operating behavior, address, and user habit information at the same time, has become a new and more effective device identification and tracking technology.
5 stages of the development of device fingerprint technology
Phase I Based on IP address. Collect information based on IP address, it is used to track buried points in some services. As the earliest device identification scheme, it is simple and easy to use, and is still the information to be collected.
IP address is a unified address format provided by the IP protocol. It assigns a logical address to each network and each host on the Internet, thereby shielding the difference in physical addresses. IP address is like home address in the real world. If you write a letter to someone, you need to know his or her address, so postman knows where to deliver the letter. Computer works like postman, it must know the unique "home address" so that it doesn't deliver the letter to the wrong person. It's just home address is written in words, while the computer's address is represented by binary digits.
With the development of dynamic IP allocation technology in LAN and mobile network, the resolution and accuracy of IP address as device identification are greatly reduced.
Phase II Based on IP address and Cookie. The unique identifier of the device is generated with the collected IP address and browser Cookie
Cookie is simple text file stored, temporarily or permanently, on the user's device. It records the user's personal information, and when the user accesses the network service again, the saved data will be used by the network service.
With the development of dynamic IP allocation technology in LAN and mobile network, the resolution and accuracy of IP address as device identification are greatly reduced; in addition, with the implementation of local storage, users can easily bypass detection by clearing local data, making its application greatly limited, and due to increasing concerns over user privacy protection, mainstream browser manufacturers have gradually phased out cookie technology.
Phase III Based on the multi-dimensional information of device. The front-end collects the user's device hardware, network, and operating environment information, and the back-end uses the collected multi-dimensional data to generate a unique ID through certain algorithm, including IDFA (advertising identifier), IDFV (supplier identifier) of iOS devices; IMEI (mobile device identifier), MAC (Ethernet physical address) of Android devices.
With the emergence of new cheating methods and tools, parameters on the device can be tampered with, which compromises the effect of unique identification of the device as specified in Phase II. Parameters on the device can be tampered with, turning it into a new device easily, which compromises the effect of unique identification of the device.
Phase IV Cross-platform and uniqueness. After stage III, there comes a unified device fingerprint ID for H5, and APP device fingerprinting (consistency of fingerprint ID of App, H5, and in the same device).
The device fingerprint at this stage needs to have higher reliability against different cheating tools to ensure the uniqueness, stability and security of fingerprint. Many new trends emerged during this phase.
First, all industries are promoting online business, the stakes are too high, resulting in a long-term fierce rivalry with illegal and semi-illegal behaviors.
Second, as mobile phone manufacturers issue stricter privacy policies, it becomes difficult to collect information such as IMEI, MAC, and IDFA. At some point, the collection rate is less than 80%, another concern is the quality of the collected data. For example, one may find the following MAC address: "00:00:00:00:00:00", "00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00", "ff:ff:ff:ff:ff:ff". Therefore, it is necessary to invest more time and energy in research to ensure the stability of fingerprinting.
Third, there are security manufacturers specialized in producing the basic components of device fingerprinting with long-term investment and research.
Fourth, new concepts emerge one after another, and people in the industry are devoted to exploring the new concept, but come up with little real technological breakthrough.
Phase V ,Cloud linkage and data precipitation. At this stage, through the cloud + terminal model, in addition to collection of more detailed information, the timeliness and security of equipment have been significantly enhanced, based on the previous experience and data precipitation of the industries. When new attack methods appear, how can fingerprinting technology respond and identify it faster.
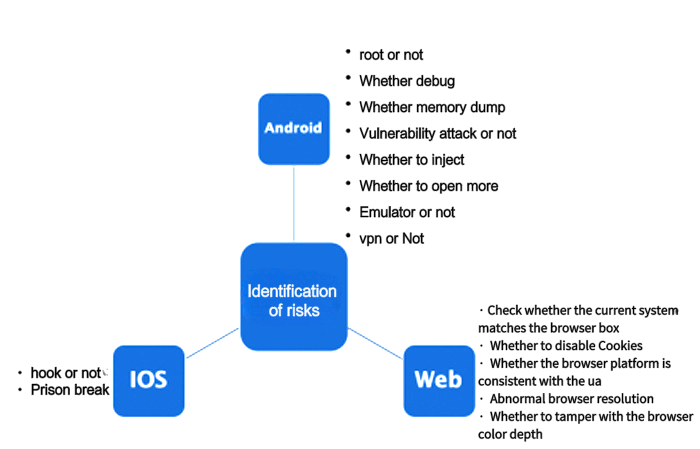
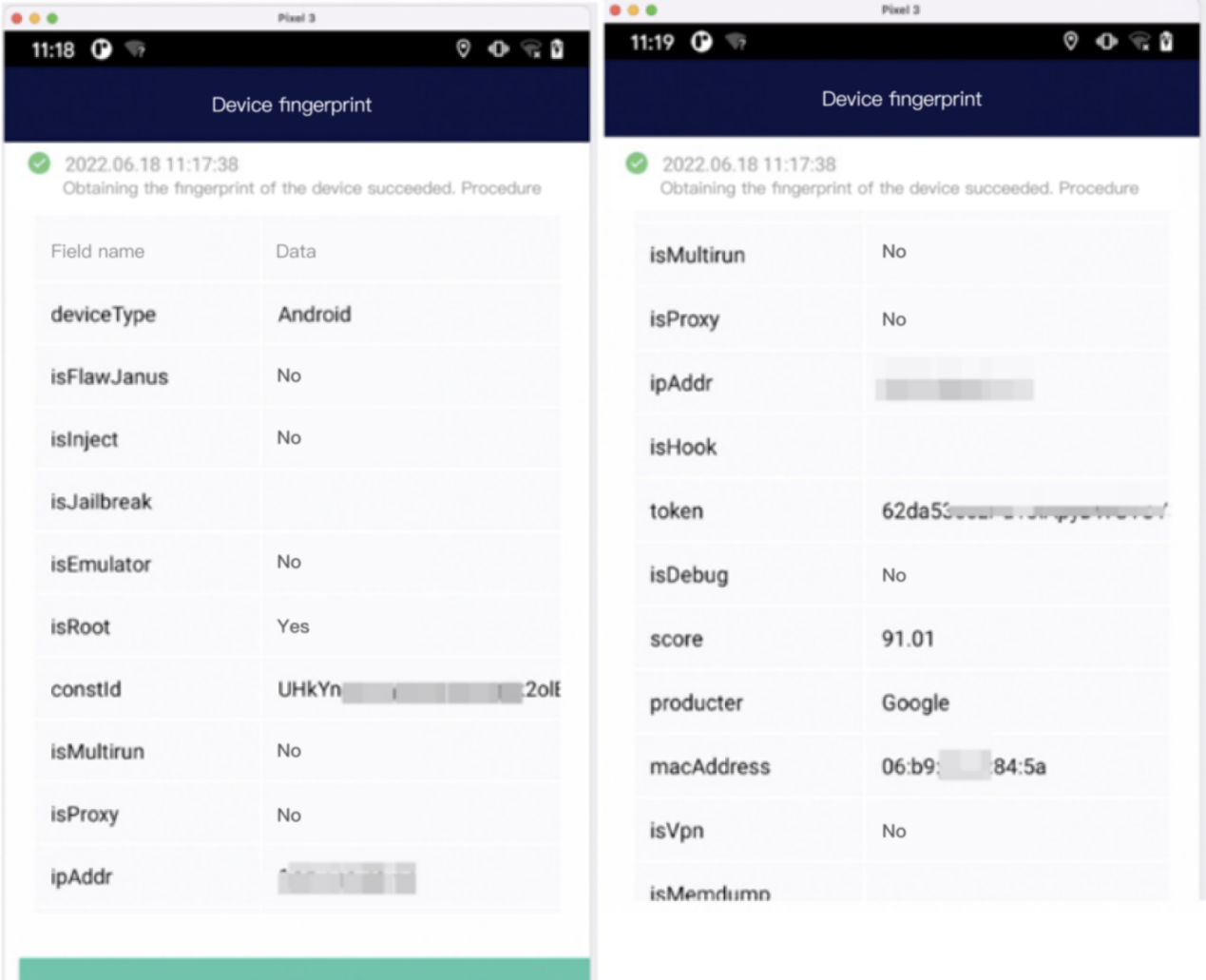
AISecurius device fingerprinting integrates business security intelligence, cloud policies and data models, by generating unique fingerprint information for Internet software and hardware, it supports Android, iOS, H5, and is capable of detecting simulator, system reinstallation, root jailbreaking, and injection attack. Built-in security intelligence center, instant trigger of 24 industry risk intelligence information, keeping security operation and maintenance personnel abreast of security situation; integrated with security cloud policy service, real-time upgrade of risk policies of the entire network, providing the latest prevention and control ideas for security operation and maintenance; equipped with AI building modules, precipitate business risk data in real time, learn threat behavior modeling with supervised and unsupervised robot, tap potential risks, upgrade and iterate prevention and control rules, and improve risk prevention and attack defense capabilities.
Four key features of this stage:
First, high recognition rate and strong security. Accurately identify dozens of risks, including identifying simulator, system reinstallation and modification, injection, and dynamic debugging to avoid being cracked and keep data authenticity.
Second, high update frequency. When encountering new attack methods, the device fingerprinting technology can be synchronized within hours or even minutes, allowing faster risk perception and accurate identification.
Third, capitalize on expert experience. The device fingerprinting has accumulated risk data in different industries and different scenarios, with rich experience in attack and defense to support fraud attacks in the cold start state.
Fourth, cloud linkage. The emergence of a secure cloud form through the cloud + terminal model, capable of responding within minutes.
Four requisite functions of AISecurius fifth-generation device fingerprinting
Stability and uniqueness are requisite for the fifth-generation device fingerprinting, as well as experience in security and protection. How to quickly conduct risk perception and offensive and defensive upgrades are essential for device fingerprinting technology. Therefore, the fifth-generation device fingerprinting has the following four requisite functions.
Stability is guaranteed to be at least 98%. Once the fingerprint is generated, it will not change, regardless of tampering with device parameters (including IMEI, MAC address, AndroidId, SIM card information, model, and brand), or disabling or clearing cache and cookies, the device fingerprinting must remain unchanged with at least 98% of stability.
Uniqueness is guaranteed to be at least 99%. The fingerprints of any two devices cannot be the same. The device fingerprint ID generated for each device needs to be 99% unique and cannot be tampered with.
As mobile phone manufacturers modify the system source code in deeper layer. For example, some enterprises deeply modify device information for the purpose of shielding device information or simulating the purpose of other manufacturers. This may cause the information collected by the device fingerprint to be shielded, modified or the parameter value is a meaningless character string under certain circumstances. It's a challenge to maintain high stability and uniqueness, which requires long-term research.
Anti-cracking is guaranteed to be 100%. The SDK code of the device fingerprint itself needs to be protected to prevent the collection logic from being cracked and data being forged, and guarantee authenticity and accuracy of source data. In addition, it requires security detection capabilities for the basic environment and runtime of the device, and capable of accurately identifying different risks, such as emulator, root, jailbreak, debugging, code injection, multi-account, and VPN proxy.
Fast responsiveness.
Business applications are exposed to the Internet, while the black and ash industry is hidden behind, so there is a certain lag in attack and defense, which requires the device fingerprint technology to have timely risk intelligence perception and prevention and control upgrade ability in the face of new attack modes and risk characteristics. The background can combine the attack and defense experience of various industries and risk data precipitation through the cloud + terminal method. Perform quick attack and defense upgrades to eliminate service risks within one attack and defense period.
Different business scenarios of device fingerprinting
As one of the basic components of the business system, device fingerprinting is widely used in scenarios such as marking, tracking, temporary credentials, analysis, and anti-fraud, and is an important part of the risk control system.
-
Dynamic anonymous tracking. The path of unregistered users accessing the website is used as user's identity without revealing the user's private data, device fingerprint technology provides accurate tracking for business.
-
Temporary user ID. In some scenarios, users are allowed to visit as tourists. At this time, the business background can obtain limited user information, and the device ID is used as a temporary user ID through device fingerprinting technology. For example, temporary user ID can be used to log in to online game, and the game progress, equipment, and level information are saved under the temporary user ID. After registered, the previous game data is automatically imported into the registered user ID.
-
Data marking and correlation analysis. In big data analysis and machine learning scenarios, device fingerprinting can be used as basic field to observe business indicator data from another perspective and perform correlation analysis. For example, through device fingerprinting ID, analyze the number of active devices, the number of new devices, the models used by users, the number and amount of transactions on the same device, and the number of users accessing the same device. When building an association, in addition to using the user's mobile phone number and card number, the device ID can also be used as node to observe the relationship between users.
4. Anti-fraud. Device fingerprinting technology is the basic application of anti-fraud, and it is effective in identifying machine attack, false registration, malicious login, multi-account, channel cheating, simulators, etc.
(1) Identify machine attack. Machine attack/script attack is generally carried out through automated scripts or tools by initiating requests to the target website in batches and automatically. Device fingerprinting technology is capable of identifying whether the request is initiated by machine or script.
(2) Identify false registration/malicious login. Device fingerprinting technology can identify account registrations using simulator, great deal of registrations on the same device within limited period, and whether the registered device is of high-risk. Similarly, in the login scenario, it can effectively identify the risk of frequent login attempts and credential stuffing on the same device, and identify whether the login device is frequently switched.
(3) Identify multi-account binding. In marketing activities, generally, the same device and the same account can only participate once. Device fingerprinting technology can quickly identify whether multiple accounts are bound to the device, and whether the same account is logged in on multiple devices.
(4) Identify channel cheating. In scenarios such as application promotion and display advertising, speculator may use technical tools to obtain promotion fee by forging traffic data. Fake machines and fake installations of real machines are identifiable through device fingerprint technology, so as to effectively track channel traffic and performance.
(5) Identify simulator/debugging. Device fingerprinting is able to detect device terminal environment and runtime risks, such as emulator, jailbreak, debugging, injection, framework attack, etc.
Application process of device fingerprinting
Device fingerprinting can be integrated into apps, small programs, and website in the form of SDK. Consider Android operating system, device fingerprinting usually uses aar package (Android Archiv, binary archive file of Android library project) to provide SDK, and also uses aar package and SO file (dynamic link library) to integrate SDK.
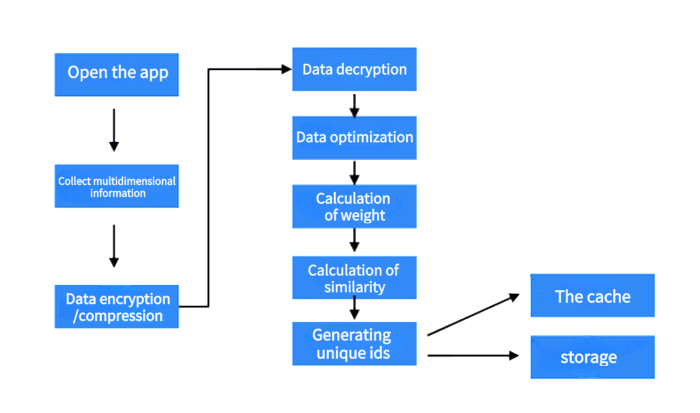
The workflow of device fingerprinting is divided into four steps: Collect and transmit, decrypt, generate unique ID, and return for verification.
-
Open App, H5, and the device fingerprinting starts to collect multi-dimensional data, and encrypt and compress the collected data to ensure data security and network transmission efficiency.
-
After receiving the collected data, the fingerprint background decrypts it, and then optimizes the initial processing of data formatting, filtering, and conversion.
-
Then, the background of device fingerprinting performs weight setting and matching on the data. The weight of some data fields involved in the fingerprint calculation will be higher than others or not involved in the calculation. Some fields are analyzed for similarity calculation, to remove duplicate, and finally a device ID is generated or associated as the fingerprint of the requested device. Finally, the generated device ID is saved for subsequent use.
-
When operating on App, H5, the device fingerprinting will match and verify the operation information, and give the verification result.
The entire process is completed in milliseconds. The most important part lies in the algorithm used to generate fingerprint ID, which requires painstaking research and practice to ensure sufficient stability and uniqueness.


