
We often see various H5 posters, product demonstrations, event promotions, and job postings. H5 can not only be seamlessly embedded in Apps and mini-programs, but can also be opened directly on the PC side as a page with an independent link address, which can be said to have good cross-platform adaptation. H5 can be used to create text, graphics, audio, and video, so it can be used for PC websites, mobile websites, microsites, Web Apps, light applications, and Web VR (popularization of virtual reality). Due to its mature technology, short development cycle, low investment and maintenance costs, and good compatibility, it is widely used in display, marketing, surveys, games, and so on.
While H5 brings convenient experiences to users, it also exposes businesses to a variety of business risks, such as link forgery, page tampering, information leakage, account theft, malicious hijacking, and scalping. According to a data from Dingxiang Defense Cloud Business Security Intelligence Center, H5 pages accounted for 46% of total attacks in website scraping data theft attacks, followed by mini-programs at 29%, then the Web at 18%; App at 5%, and other platforms at 2%.
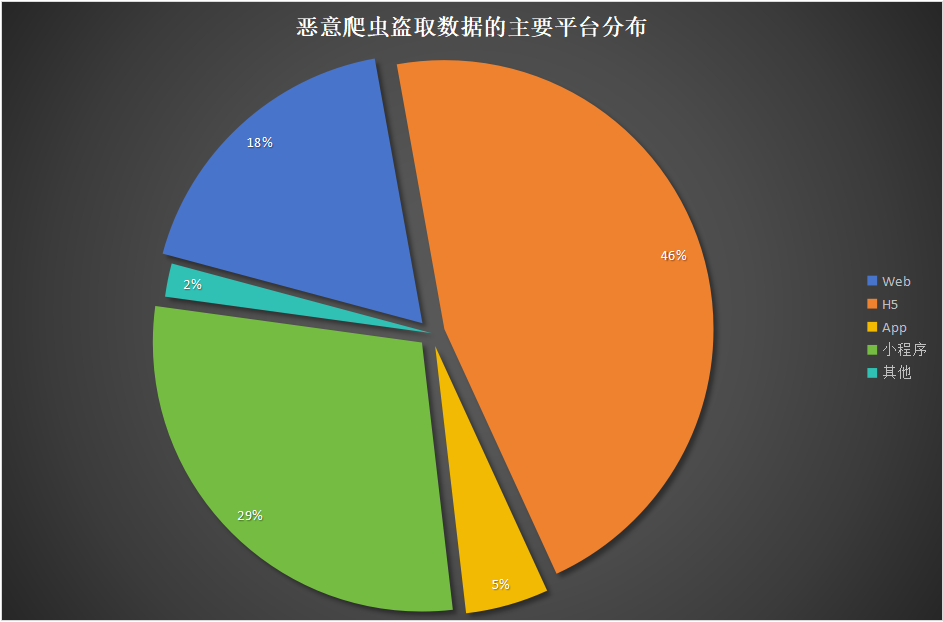 In addition to website scraping data theft, H5 is also a hot spot for attacks such as scalping, fake account registration, and dictionary attacks.
In addition to website scraping data theft, H5 is also a hot spot for attacks such as scalping, fake account registration, and dictionary attacks.
Why H5 Pages Have Become a Preferred Platform for Illegal Attackers
The Dingxiang Defense Cloud Business Security Intelligence Center analyzed that H5 pages have become a preferred platform for illegal attackers due to the following issues:
Page code is often in "cleartext" format. The development language of the H5 platform is JavaScript, and all business logic code is executed directly on the client in a certain "cleartext" way. This means that attackers can easily obtain sensitive data such as account numbers, passwords, and personal information by simply inspecting the page code. The underlying architecture has security vulnerabilities. Browsers have many restrictions on the H5 development language JavaScript, which also weakens the H5 security protection capabilities at the business layer to some extent. For example, attackers can exploit vulnerabilities in JavaScript to steal sensitive data or take control of user accounts. There are many automation tools available publicly. The H5 page structure is transparent, and attackers can construct parameters and submit requests using scripts to achieve complete automation. These tools can effectively automate pages without having to reverse the JS code, making it easier for attackers to carry out malicious activities such as website scraping or scalping. Operators have a weak security awareness. Many operators lack a systematic understanding of the security of H5 pages. They pursue short-term and quick online business, and they do not build a complete protection system for the H5 channel before launching marketing business involving funds. This makes it easier for attackers to exploit H5 pages to steal sensitive data or commit fraud.
Obfuscation: The Best Security Measure for H5 Pages
To address the security risks of H5 pages, a dedicated obfuscation tool is needed to increase the difficulty of cracking, effectively increasing the cracking cost of attackers.
H5 code obfuscation is an important means of H5 security protection, which can protect the core code and sensitive data of H5 applications that need to be protected. It refers to modifying the H5 code to make it difficult to read and understand, thereby increasing the difficulty of malicious attackers to perform reverse analysis. At the same time, it effectively protects the security of H5 applications, preventing malicious attackers from stealing core code and sensitive data.
The common methods of H5 code obfuscation are mainly divided into four categories:
Identifier obfuscation: Modifying the identifiers in the code (such as variable names and function names) to make them difficult to identify. Control flow obfuscation: Modifying the control flow structure in the code to make it difficult to understand. Data structure obfuscation: Modifying the data structure in the code to make it difficult to identify. Code compression: Compressing the code to make it difficult to read. Dingxiang H5 Code Obfuscation
Dingxiang H5 Code Obfuscation converts strings, numbers, and regular expressions in the code to strings, then randomly splits the strings, and randomly encrypts the strings after splitting them using a reversed order or random key to encrypt the functions. At the same time, the order of the functions is shuffled, and the obfuscation algorithm is automatically updated and the JS is updated to the CDN, thus ensuring the security of the H5 page.
Dingxiang H5 Code Obfuscation supports a variety of obfuscation methods, including string encryption, string splitting, variable name obfuscation, control flow obfuscation, and constant extraction. It also provides a variety of security features, such as domain binding and anti-debugging. It is compatible with a variety of H5 code runtime environments, such as Android, iOS, WeChat Official Accounts, mini-programs, and web pages. It provides command-line tools and packaging plugins for webpack/gulp, seamlessly connecting to various packaging processes.
Dingxiang: Adaptive Code Obfuscation Technology Based on AI
As the latest upgrade of Dingxiang H5 code obfuscation, Dingxiang AI adaptive code obfuscation is based on graph neural network technology. By deeply analyzing and extracting code features, it can automatically select suitable methods for obfuscation according to the characteristics of different code blocks. It can significantly improve the difficulty of reverse analysis of the code and effectively reduce the calculation performance consumption by 50%. Through the encryption obfuscation engine, H5 code can be encrypted, obfuscated, and compressed to greatly increase the security of H5 code and effectively prevent the product from being copied and cracked by black and gray industries.
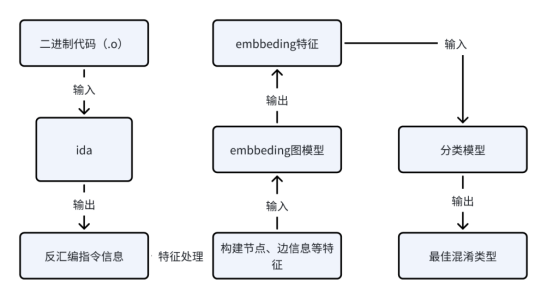
Traditional H5 code obfuscation methods are often general, with a unified structure and logic, and are applicable to all types of H5 code. Once it is cracked by a reverse engineering tool, the entire H5 page will be cracked and invaded. Dingxiang AI adaptive code obfuscation can obfuscate different code blocks, such as short code blocks, long code blocks, simple code blocks, and complex code blocks. Based on deep analysis and extraction of code features, it can automatically select suitable methods for obfuscation, which can significantly improve the difficulty of reverse analysis of the code.
In addition, in traditional H5 code obfuscation, the calculation performance may be sacrificed for the obfuscation effect. For example, for a small piece of code, using instruction replacement obfuscation method can achieve good obfuscation effect, and the obfuscated code has relatively low calculation performance consumption; but for a whole long piece of code, the obfuscation effect of the method with relatively low obfuscation degree is often poor, so it is often forced to choose the obfuscation method with relatively high obfuscation degree, such as false control flow + code block segmentation obfuscation method, but these methods often have a very high consumption of calculation performance, which also leads to low code running efficiency. Dingxiang AI adaptive code obfuscation can reduce the calculation performance consumption by about 50% compared with traditional obfuscation methods while ensuring the obfuscation effect.
Overall, the advantages of Dingxiang AI adaptive code obfuscation mainly lie in the following aspects:
More advanced obfuscation effect: Dingxiang AI adaptive code obfuscation can automatically select suitable methods for obfuscation according to the characteristics of different code blocks, which can significantly improve the difficulty of reverse analysis of the code. Lower calculation performance consumption: Dingxiang AI adaptive code obfuscation effectively reduces the calculation performance consumption while ensuring the obfuscation effect, which improves the running efficiency of H5. Higher compatibility: Dingxiang AI adaptive code obfuscation supports a variety of H5 code runtime environments, such as Android, iOS, WeChat official accounts, mini programs, and web pages, with high compatibility. Dingxiang AI adaptive code obfuscation can be widely applied to various H5 pages, especially in the financial, e-commerce, and gaming industries. It can effectively prevent malicious attackers from performing reverse analysis, protect the core code and sensitive data of H5 applications, and thus ensure business security.


