
On February 15, 2024, cybersecurity company Group-IB announced the discovery of a new malware called "GoldPickaxe." The iOS version of this malware tricks users into performing facial recognition and submitting identification documents, then uses the user's facial information to create deepfakes.
Using the fake facial video created by deepfake, fraudsters can log into the user's bank account, intercept the mobile verification SMS sent by the bank, and then perform transfers, consumption, and modify the account password.
The iOS version of "GoldPickaxe" places great emphasis on social engineering, and its description of sensitive information acquisition and collection is very detailed. For example, before taking a picture of the user's face, the malware will prompt "Please keep the camera stable" and "Please blink", and even uses Google's ML kit for face detection. It also requires identification documents or bank card information. The software will prompt the victim to upload the front and back of the ID or bank card, and automatically open a series of views with prompts to guide the victim to perform the necessary steps. Once the facial information and ID photos are taken, they will be automatically sent to the fraudster's server.
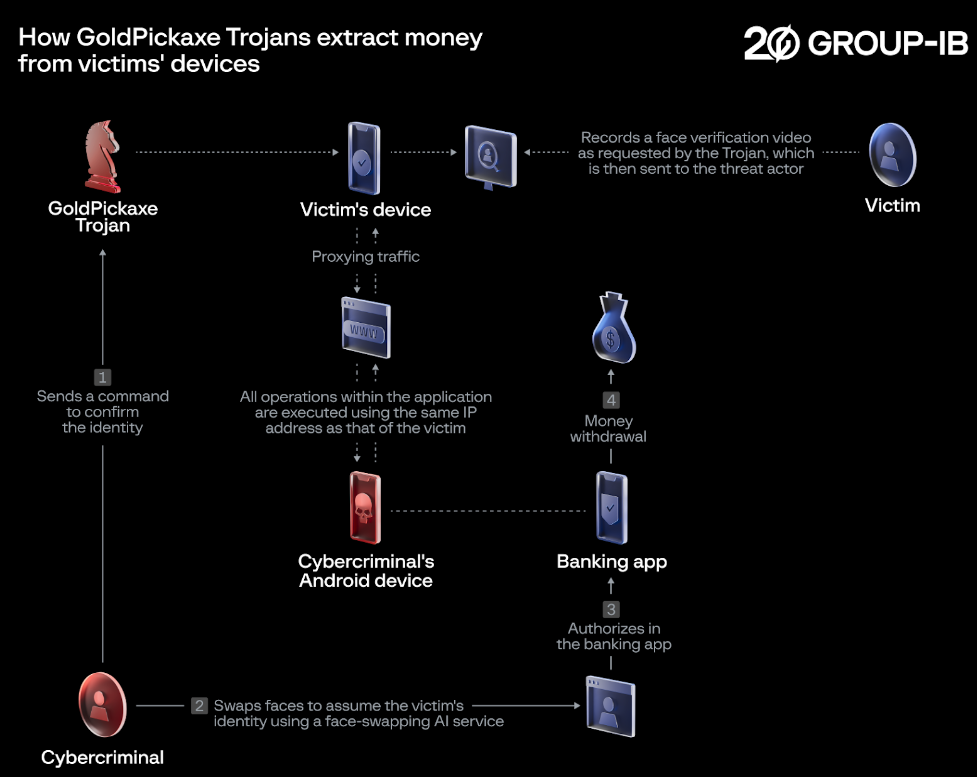
The Android version of "GoldPickaxe" has more features. In addition to collecting and stealing the victim's facial information, ID card, bank card information, etc., the Android version can also search for more facial pictures in the phone's album and request facial recognition and other authorization services from the bank app.
Infection: How Does This AI Virus Infect Users' Phones?
According to the disclosure of the Thai police, the fraudsters using the "GoldPickaxe" malware first contacted the users through social software, emails, and collected text messages, claiming that elderly relatives are eligible for additional pension benefits, and attached a link to download the malware, guiding users to download and install.
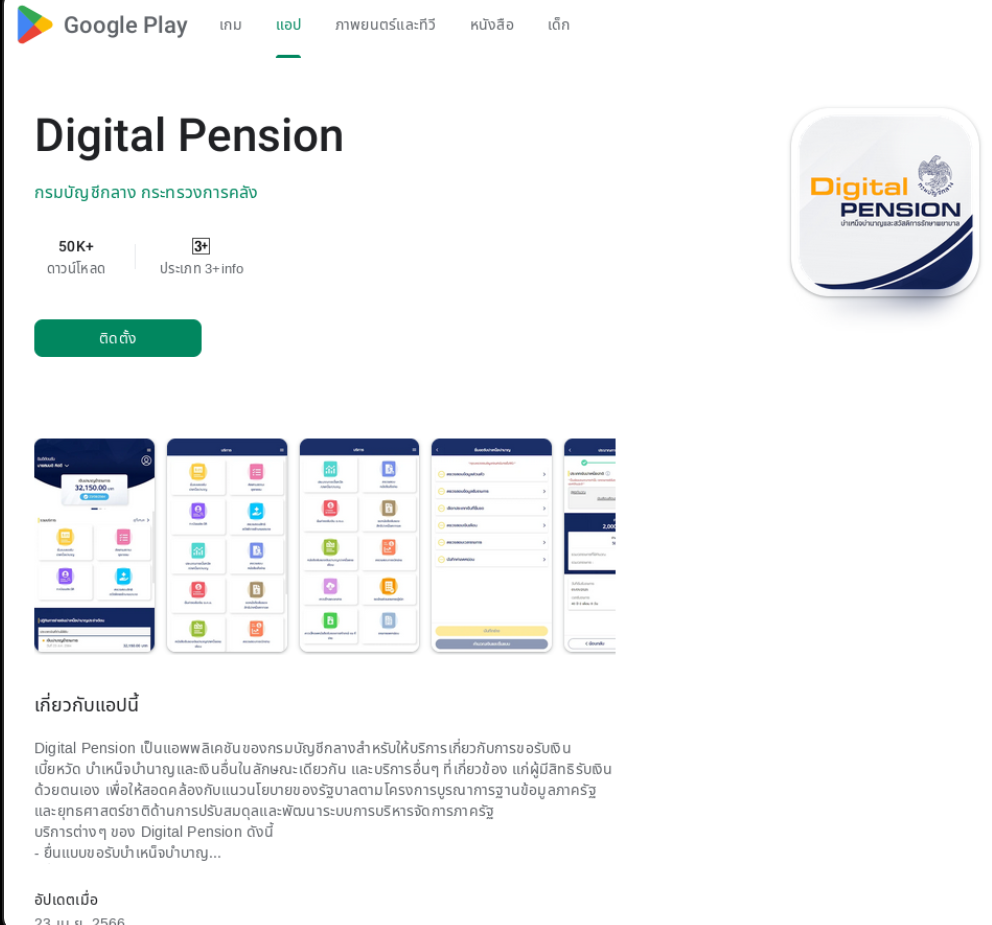
Researchers from security company Group-IB have discovered that the Android version of "GoldPickaxe" can disguise itself as more than 20 different counterfeit apps from government, financial and utility companies, such as a counterfeit Thai "Digital Pension App". In addition, fraudsters also create fake government and financial institution websites to provide downloads of the "GoldPickaxe" Android malware.
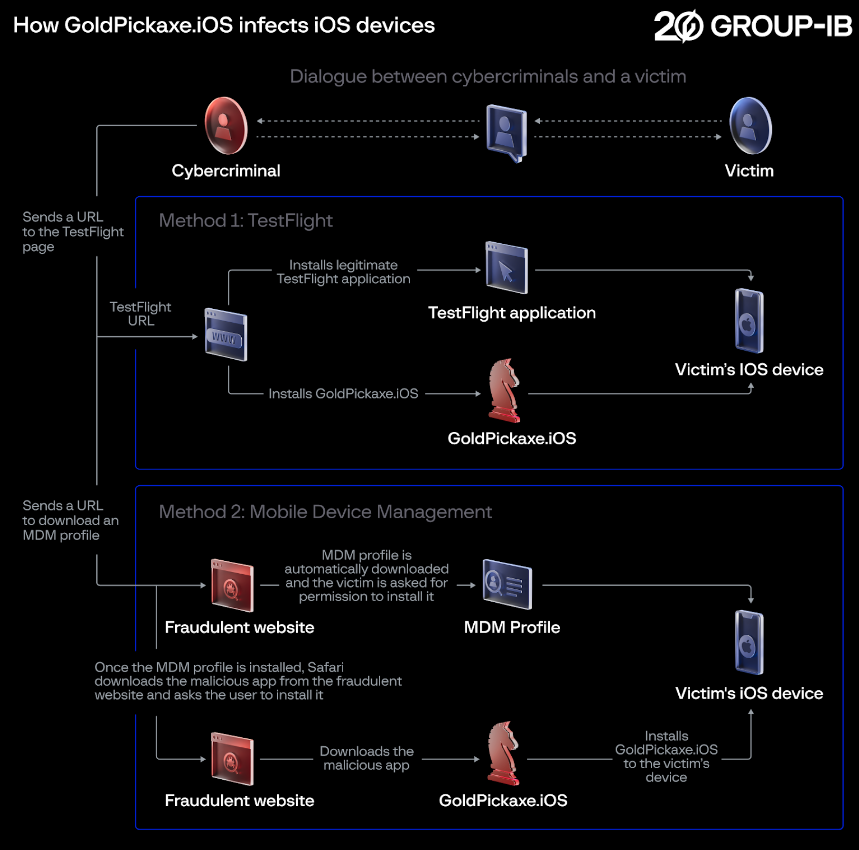
 Apple's iOS system has higher security and stricter control over app permissions. To prevent malware from entering, Apple only allows apps to be distributed through the Apple App Store. The iOS version of the "GoldPickaxe" malware bypassed Apple Store's review in two ways.
Apple's iOS system has higher security and stricter control over app permissions. To prevent malware from entering, Apple only allows apps to be distributed through the Apple App Store. The iOS version of the "GoldPickaxe" malware bypassed Apple Store's review in two ways.
-
Abuse of TestFlight. TestFlight is a software testing platform for iOS systems. Based on TestFlight, developers can test their Beta apps on iOS (iPhone, iPad, Mac, Apple TV, etc.). iOS devices can directly install Beta apps through TestFlight without downloading through the Apple Store.
-
Abuse of Mobile Device Management (MDM). MDM is a service of iOS that helps IT administrators deploy and manage devices in an enterprise environment, and ensure device security and compliance. It can remotely manage iOS devices (iPhone, iPad, Mac, etc.) within the enterprise. Developers choose an MDM server (including Apple's DEP and third-party MDM solutions) and obtain an MDM certificate. Then submit for review, and the MDM service permission will be opened after the review is passed. Then manually add the company's MDM server address in the specified iOS device, or add the specified device through the management interface of the MDM server. Devices added to the company's MDM can be remotely managed, and apps, configuration files, data collection, function restrictions, and even device locks and device information can be directly installed on the specified device.
Fraudsters induce iOS users to install TestFlight or download MDM configuration files, and then they can install the iOS version of the "GoldPickaxe" malware on users' iPhone, iPad, Mac and other devices.
Features: What Are the Harmful Features of This AI Virus?
The Group-IB security report describes in detail the harm of the "GoldPickaxe" malware.
-
The "GoldPickaxe" malware has both iOS and Android versions. Currently, only groups in Vietnam and Thailand have been found to be affected by the malware.
-
The "GoldPickaxe" malware does not directly steal users' bank funds, but only collects and steals users' sensitive information such as facial information, ID documents, and bank cards, and intercepts mobile phone text messages.
-
The "GoldPickaxe" malware will use the stolen facial information to create deepfakes, create fake victim videos, and then directly log in to the victim's bank account to steal money.
-
The iOS version of "GoldPickaxe" is spread through Apple's TestFlight or by social engineering victims to install MDM configuration files; the Android version of "GoldPickaxe" is spread through mobile phone text messages, emails, phishing websites and Android markets.
-
Security researchers have also discovered several new variants of the "GoldPickaxe" malware. Among them, a new variant called "GoldDiggerPlus" can forge alarms and customer service. When the victim clicks the fake alert to contact the customer service button, the malware will try to find a free carrier to call. It's as if cybercriminals are running a real customer service center.
-
Social engineering is used throughout the "GoldPickaxe" malware. The malware is associated with the cybercrime group GoldFactory and is closely related to the "Gigabud" malware that ravaged financial institutions in 2023.
Defense: How Do Banks and Individuals Defend Against AI Viruses?
Dingxiang Defense Cloud Business Security Intelligence Center previously warned that with the wide application of AI in various industries, the security threats it brings have also attracted people's attention. AI is becoming a new means of threat. Attackers using AI technology will bring unprecedented risks to enterprises and individual users, and listed the five trends of business fraud risks in 2024: new attacks brought by AI are increasing exponentially, accounts and identities are more difficult to distinguish, and data crawling is still rampant , Account theft and impersonation will become more common and difficult to prevent, and internal data breaches.
**The main reasons behind this growth trend are the continuous advancement of technology and social engineering. As more and more people turn to online and mobile channels for shopping, frauds
Security Recommendations for Financial Institutions
Dingxiang Defense Cloud Business Security Intelligence Center recommends that financial institutions need to ensure the security of their apps and educate their customers about security.
- Strengthen App security detection and ensure security and compliance.
Dingxiang App Hardening, which was the first to perform iOS source code free hardening, supports Android, iOS, H5, mini programs and other platforms. It has unique cloud strategy, business security intelligence and big data modeling capabilities. It can effectively defend against attack threats such as memory injection, Hook, debugging, injection, multi-open, memory dump, simulator, secondary packaging and log leakage, prevent App from being invaded, tampered, cracked, secondary packaged and other malicious damages, protect 16 kinds of data and files of Android, and provide 7 kinds of encryption forms.
Dingxiang App Hardening can perform security detection on existing Apps, discover the risk vulnerabilities existing in the applications and make targeted repairs and rectifications, protect sensitive data, code obfuscation, code integrity, memory data, etc., avoid the security impact of system vulnerabilities on the application itself from the source, prevent data information leakage, and ensure App security. It can also provide security monitoring for the operation of mobile applications, and monitor the terminal devices, operating environment and operation behavior of mobile applications in real time, helping App to establish a security system for monitoring, early warning, blocking and tracing of runtime risks.
In response to the risk of financial App face being stolen, Dingxiang Business Security Perception and Defense Platform is an active security defense platform based on advanced technologies such as threat probes, stream computing and machine learning. It integrates device risk analysis, running attack identification, abnormal behavior detection, early warning and protection and disposal. It can detect malicious behaviors such as camera hijacking and device counterfeiting in real time, and effectively prevent and control various risks of face recognition system. It has the characteristics of threat visualization, threat traceability, device association analysis, multi-account management, cross-platform support, active defense, open data access, defense customization and full-process prevention and control.
-
Pay close attention to various threat warnings, take security measures, and be able to respond quickly to new threats.
-
Educate users about security and improve
their security awareness by explaining fraud cases.
Security Recommendations for Individual Users For individuals, Dingxiang Defense Cloud Business Security Intelligence Center recommends that you must download Apps from formal channels and always maintain safe usage habits.
-
Do not click on unfamiliar links received in mobile phone text messages, social software, or emails.
-
Do not disclose sensitive information such as SMS verification codes, bank cards, and ID cards to others.
-
When receiving strangers calls or text messages, be sure to stay calm. If you feel suspicious, please call the police immediately.
-
Be sure to download Apps through the AppStore, Android Market, and the official website of the financial institution. Do not download through third-party platforms or links sent by others.
-
Do not install unfamiliar, unknown, or unfamiliar Apps.
-
When installing Apps, be sure to carefully check the permissions requested by the App and be highly vigilant when the App requests auxiliary functions.
7 When contacting a financial institution, be sure to call the inquiry number. Published by the official channel.


