
To a certain extent, device fingerprints are as important to people as ID cards.
Why do you say that?
Most of you have probably experienced something like this:
When viewing a short video, as long as we like a certain video, the system will recommend more similar videos when viewing the video next time; when you browse a product on a certain shopping software, the shopping software will Items related to the search term appear.
You think you are dominated by the algorithm, but in fact, the fingerprint of the device "betrayed" you.
A device fingerprint, as the name implies, is a device feature or a unique device identifier that can be used to uniquely identify the device. And have a certain offensive and defensive capabilities, with the ability to monitor the equipment environment.
For some websites, being able to accurately identify a certain user, browser, or device is a very tempting ability, and it is also a strong requirement.
 For example, for advertising companies or search engines, device fingerprints can be used to know what the user has searched for before and what his hobbies are, so that the search results can better meet the user's needs in the search results; for banks, e-commerce, etc. For organizations with higher security requirements, this technology can be used to detect changes in the user environment and devices that are logging in, thereby preventing malicious requests such as account theft and password cracking.
For example, for advertising companies or search engines, device fingerprints can be used to know what the user has searched for before and what his hobbies are, so that the search results can better meet the user's needs in the search results; for banks, e-commerce, etc. For organizations with higher security requirements, this technology can be used to detect changes in the user environment and devices that are logging in, thereby preventing malicious requests such as account theft and password cracking.
Of course, for black and gray products, this technology can also be used to change user identities. Generally speaking, black and gray production will cause huge economic losses to enterprises in a short period of time through equipment ranching cheating, simulator cheating, manual cheating and other attack methods.
However, the traditional equipment identification technology mainly relies on a single information source, and cannot effectively identify and judge black and gray products. therefore
Enterprises urgently need a new device identification and tracking technology to distinguish between normal users, malicious users and even fraudulent gangs, so as to protect the security of enterprise assets.
Today, we will start with the anti-tampering and anti-hijacking functions of the fingerprint of the top image device.

"Never trust" risky users
As mentioned above, device fingerprints are equivalent to a person's second identity authentication. Once it is tampered with or hijacked, the consequences can be imagined.
Generally speaking, black and gray products will tamper with data by flashing, changing the machine, changing the IMEI, MAC and other means, thereby causing the company to suffer losses. So, how does Aisecurius' device fingerprint technology discourage black and gray products?
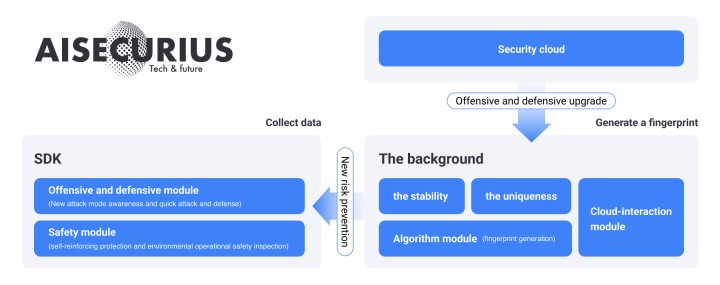
The current device fingerprint technology uses multi-dimensional device-side information to complete device identification. It collects the characteristic information of the terminal device, and on the basis of analysis and identification, performs correlation calculations on each group of characteristic information collected from the terminal device through a similarity algorithm to generate a unique device fingerprint ID to identify the terminal equipment. From the technical method of implementation, it can be divided into active device fingerprinting and passive device fingerprinting.

So, in terms of anti-tampering and anti-hijacking, how does the fingerprint technology of top image devices realize?
The first is identification. Generally speaking, normal users will not easily tamper with information. When a user keeps tampering with information, it is necessary to keep track of its behavior track and then determine whether it is a risk user. Once the identity of the risk user is determined, it also loses If the qualification of "trusted" is obtained, then the system will intercept the user.
The next step is the moment when the top image device fingerprints show their talents. As mentioned above, the device fingerprint itself already has the ability to analyze and identify the characteristics of the device, but to deal with black and gray products, only one layer of protection is not enough. The top image method It's locked and locked.
When the system determines that a user is a risk user, the device fingerprint will analyze and identify the collected device information through an algorithm.
The device fingerprint system is divided into three functional modules: device fingerprint front-end collection, device fingerprint service, and device fingerprint console, and has a supporting data storage module.
The server-side device fingerprint production algorithm is mainly based on the information collected by the client (including web, android, and ios). For the collected device information, the back-end algorithm will divide it into strong feature data and weak feature data. If the terminal device is at risk, the system will display the risk label and score the device based on multiple dimensions such as device environment, vulnerability, and existing risks. The lower the score, the higher the risk.

Digital business risks are becoming more diverse
Behind the anti-tampering and anti-hijacking functions of device fingerprints is the greater risk of enterprises-digital business security.
With the deepening and popularization of digitalization, businesses are becoming more open and interconnected. The key data, user information, infrastructure, and operation process of enterprises are all in an environment with blurred boundaries and increasingly open. Businesses involving profit streams and high value-added businesses face various security risks and may suffer losses at any time, which in turn affects business operations and develop.
On the one hand, there are various forms of business security risks. In business scenarios such as e-commerce, payment, credit, account, interaction, and transaction, there are various types of fraudulent behaviors; on the other hand, fraudulent behaviors are increasingly specialized and industrialized. And it has the characteristics of gangs, complexity, concealment and contagion.
Therefore, the mature device fingerprint technology has become one of the key technologies for big data risk control of every anti-fraud enterprise.


