At the end of July, the National Financial Regulatory Administration issued a risk alert about new types of telecom network fraud, reminding the public to be wary of scams involving "screen sharing" and "AI face-swapping with voice imitation." The notice urged people to enhance their awareness of risk prevention and identification to protect their finances.
The notice pointed out that in "screen sharing" scams, fraudsters use excuses such as "increasing credit card limits," "canceling bad loans under your name," "terminating insurance services," "flight delay refunds," or "offering gifts" to send texts or make phone calls to individuals. They trick consumers into downloading specific chat or online video conference software and instruct them to enable the "screen sharing" feature. This allows the fraudsters to "monitor" the consumer's phone or computer screen in real-time while "guiding" them through actions such as linking bank cards or changing passwords. In doing so, they gain access to personal banking information, passwords, and verification codes, eventually stealing funds from bank accounts.
In June, the Ministry of Public Security released the top ten telecom network fraud cases, one of which also involved "screen sharing" fraud. In May 2024, a woman named Du in Wuxi, Jiangsu, received a video call at home from someone claiming to be a police officer from the criminal investigation team of the Wuxi Public Security Bureau. The person on the video, dressed in uniform, claimed that Du's bank card was involved in a money laundering crime and that she needed to cooperate with an investigation. Du followed the instructions, downloaded meeting software, and enabled screen sharing to allow the "police officer" to verify the funds in her bank account. The fraudster then told Du that she needed to transfer the funds in her account to a "safe account" to prove her innocence. During the process, the "police officer" also instructed Du to take out a 150,000-yuan loan from the bank and transfer it to the "safe account" to show that her financial transactions were normal. It wasn't until her family intervened that Du realized she had been scammed.
In such cases, fraudsters deceive victims into enabling screen sharing on their phones, leading to the exposure of account passwords. Even without directly asking for information, fraudsters can view everything on the victim's phone, including the characters typed when entering passwords and the verification codes received, allowing them to transfer funds from the victim's bank accounts.
How Attackers Use "Screen Sharing" to Commit Fraud
One of the scenarios where the "screen sharing" feature is applied involves using the internet to project the screen information of one device in real-time to another device. This includes all content displayed on the screen, such as app screens, SMS pop-up notifications, WeChat messages, other app notifications, account and password entry, unlocking procedures, and other real-time operations. Originally designed for user convenience, this feature has become a tool for fraudsters to profit.
According to an analysis by Dingxiang's Cloud Security Intelligence Center, fraudsters use the following four steps to carry out "screen sharing" scams:
Step 1: Obtaining information and gaining trust.
Fraudsters use illegal channels to acquire victim information and impersonate law enforcement, shopping platform customer service, or staff from student loan cancellation services. They accurately match the victim's situation to gain their trust.
Step 2: Deceiving victims into enabling "screen sharing."
Using certain apps (e.g., QQ, Tencent Meeting, DingTalk) with built-in screen sharing features, fraudsters can monitor the victim's phone operations in real time.
Step 3: Logging into online banking and monitoring SMS verification codes in real-time.
Fraudsters first instruct the victim to download an app and enable screen sharing. They then use previously obtained bank card details to log into the victim's online banking and initiate a transfer while monitoring incoming SMS verification codes in real-time.
Step 4: Stealing funds.
Fraudsters initially trick the victim into making a transfer voluntarily. If the victim realizes the scam or hesitates, the fraudster uses the intercepted verification codes to complete the transaction, transferring the funds without the victim's awareness.
Dingxiang Device Fingerprinting Can Prevent "Screen Sharing" Risks
On Android devices, "screen sharing" is implemented through the MediaProjection service. MediaProjection is a technology available for developers on Android 5.0 and above, enabling them to capture or record screens. When a user applies to use the MediaProjection service, Android will pop up a permission request. Only after the user clicks "Confirm" can the screen sharing or recording begin.
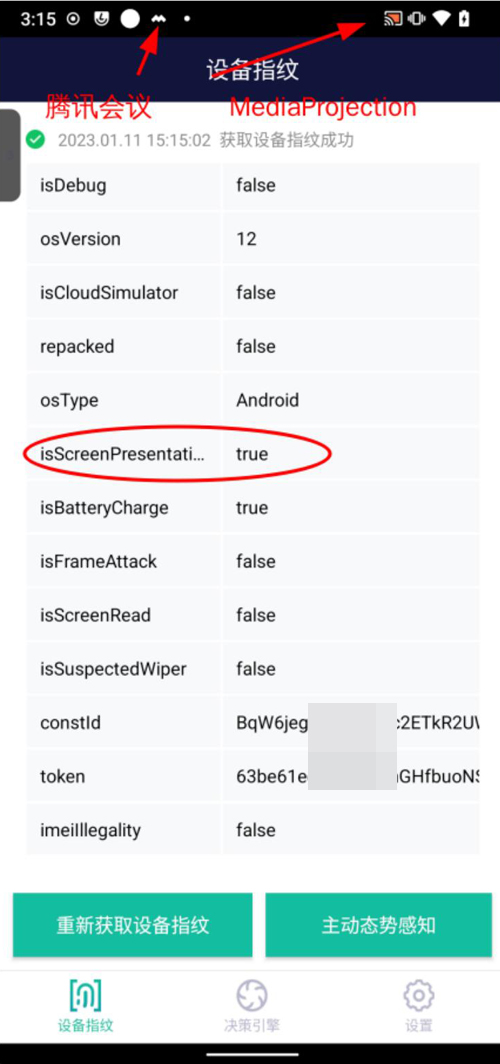
Dingxiang Device Fingerprinting can detect the activation of screen sharing through apps like DingTalk and Tencent Meeting in real-time and immediately issue an alert to warn users about potential risks. When MediaProjection is activated, the system automatically creates a virtual display, and Dingxiang Device Fingerprinting detects this additional screen interface, confirming that the device is in a "screen sharing" state. It then promptly reports this status to the risk control center. The risk control center will issue a warning, reminding the user of potential danger and urging them to stay cautious.
Dingxiang Device Fingerprinting collects and analyzes hardware, software, and behavioral data to uniquely identify and recognize each device. This technology can identify maliciously controlled devices such as virtual machines, proxy servers, and emulators. It analyzes whether a device is showing suspicious behavior, such as multiple account logins, frequent IP address changes, or frequent modifications to device attributes that do not align with typical user habits. By tracking and identifying fraudulent activities, it helps prevent fraud. Dingxiang Device Fingerprinting can also be used as an additional factor for identity verification, enhancing the security of user login and transaction processes. By recording and comparing device fingerprints, it can distinguish between legitimate users and potential fraudsters. It supports Android, iOS, H5, WeChat public accounts, and mini-programs, effectively detecting risks such as emulators, rooted/jailbroken devices, system modifications, and injection attacks. It boasts fast detection, efficient risk identification, over 99% stability, and 100% uniqueness.
How Users Can Prevent "Screen Sharing" Risks
"Screen sharing" is increasingly being used in various forms of fraud. The final step in these scams typically involves asking the victim to use or download video conferencing software that offers "screen sharing" functionality. The goal is to spy on the victim's device to obtain critical information like bank account passwords.
- Do not activate the "screen sharing" feature on Android phones without verification.
- Decline any "screen sharing" invitation from strangers. Do not use the "screen sharing" function with strangers, as they can see all your actions, including when you enter passwords.
- Be extra cautious with private information, especially bank account passwords and verification codes. Never disclose this information to any stranger.
In short, if you receive a suspicious video or phone call, remain calm. You can use the excuse of a bad signal to hang up, then immediately verify the situation through other means to avoid responding directly to possible scam content.